Deliverability
DKIM setup: How to create, configure, and set up DKIM in 3 easy steps
DKIM (DomainKeys Identified Mail) is an email authentication protocol that helps to prevent email spoofing and phishing attacks, as well as improving email deliverability by increasing the likelihood that your legitimate emails will reach the intended recipients’ inboxes. We’ll explain how it works and how to set up DKIM for better email security and deliverability.

PUBLISHED ON
You didn’t become an email marketer because you wanted to dive into complicated code all day. Ugh. And when you hear all these weird sounding acronyms like DKIM, SPF, and DMARC, your first instinct is probably to run for the hills.
But then, you learn about the deliverability implications of not setting up appropriate email authentication protocols, and you realize its something worth paying attention to. Even more so now that Gmail and Yahoo have announced changes that will make this a requirement for all bulk senders in 2024.
DKIM authentication can’t guarantee a 100% delivery rate – probably nothing can. But it is critical to get more emails delivered to the inbox.
Originally developed at Yahoo, DKIM (DomainKeys Identified Mail) has become a global standard in email security. Together with its sister SPF, DKIM is a necessary tool for anyone serious about email, especially those sending email blasts. In this post, we’ll show you how to set up DKIM and make your outgoing email more secure.
Table of content
History of DKIM
DKIM vs DMARC
DKIM encryption keys
What is a DKIM selector?
Step #1: Setting up configuration of DKIM to generate the key pair
Step #2: Placing the public key as a TXT record in the DNS settings
Step #3: Generating and saving the signature
What is DKIM?
DKIM is an email authentication protocol. It functions like a digital signature by inserting code in the email header, which then gets encrypted. DKIM provides a way for mailbox providers (MBPs) like Yahoo and Gmail to verify that an email really does originate from an authorized user of the sending domain listed.
This problem has gotten worse in recent years in a large part because of email spoofing. We’ve all been on the receiving end of this insidious scam; when you receive emails claiming to be from big companies like PayPal, Amazon, FedEx, or your bank, telling you your package hasn’t been delivered, or your password has changed, or this invoice is unpaid, that’s spoofing. It’s a scammer pretending to be a real company, trying to get you to click on attachments or give up sensitive personal information.
DKIM helps protect recipients from scams by allowing mailbox providers to distinguish real senders from fake ones. It also ensures that the email hasn’t been tampered with during transmission.
And this is one reason email delivery rates should not be 100% across the board. Some emails should be blocked – the illegitimate ones. Your job is to make sure your emails get delivered, and DKIM makes a huge difference in helping that happen.
History of DKIM
DKIM originated around 2004 when various email service technology companies began to look for a way to protect email users from spam. Yahoo created a tool called Domain Keys and Cisco developed one called Identified Internet Mail.
When these two similar tools were combined, DKIM was born.
Since then, DKIM has grown in use and popularity as a method for authenticating emails by verifying the sender is who they claim to be. Here are more historical highlights from the advancement of DKIM.
If you’ve ever sent emails using an email platform like Mailjet, you know that you can write anything you want in the ‘From’ field. You can also create an endless stream of email addresses to enter as the sending email. But once mailbox providers – the Yahoos and Gmails of the world – know and recognize PayPal’s digital signature, all the scammers pretending to be PayPal are easy to identify.
DKIM helps mailbox providers decide which emails to block, which ones to filter into the spam folder, and which ones to deliver.
DKIM vs DMARC
These are actually very different. DKIM is closer to SPF than it is to DMARC, which we’ll get to in a moment. First, what is SPF? We’re not talking about sunblock ratings here. SPF stands for “sender policy framework.” It’s another email authentication tool that lets domain owners determine which IP addresses can send emails using that domain.
This matters because you can only use DMARC once you have DKIM and SPF set up.
What is DMARC? It stands for domain-based message authentication, reporting, and conformance.
The idea behind DMARC is, what happens if an email fails SPF and DKIM. What should Yahoo do? While DKIM is meant in part to prevent email spoofing, it doesn’t fully accomplish that if the mailbox provider doesn’t block the scam emails.
DMARC tells mailbox providers what to do if an email fails both of those authentication protocols. This is why it usually gets referred to as your ‘DMARC policy.’ It’s what you want incoming mail servers to do if an email fails to pass DKIM or SPF.
You can specify one of three options – reject, quarantine, or none.
Reject means just what it sounds like – the email will not be delivered and no one will ever see it. This is what you want if everyone agrees this email is a scam.
Quarantine means the recipient won’t get the email, but an administrator can still see it so they can assess the message. You might want this option to understand what sorts of threats against your email reputation exist.
None means the message still gets delivered. When you first start using DMARC, this is recommended so you can see which emails are failing authentication. You don’t want to instantly have them all rejected, because if something isn’t set up correctly with DKIM or SPF, your own legitimate emails could be failing authentication. Using none will allow you to fix those problems without affecting your email deliverability.
URGENT: Google and Yahoo recently announced that as of February 2024, DKIM and SPF authentication will be mandatory for bulk email senders. These senders will also need to have DMARC set up at p=none policy. For more information about how to implement DKIM and DMARC and comply with the upcoming mandates, check out our articles How to handle SPF andWhat is DMARC and how it works.
Why should you use DKIM?
The main reason you should use DKIM verification is pretty simple: Along with SPF and DMARC, these are the main email authentication methods for verifying the identity of senders. They’re some of the most effective ways to prevent phishing and email spoofing, which has seriously eroded brand trust in the inbox.
But this is not DKIM’s only advantage. In fact, the implementation of these protocols alsoimproves email deliverability by strengthening your email reputation with mailbox providers and spam blocklists.
Your emails will be confirmed as legitimate for your subscribers by their mailbox providers, which improves the chances of your emails reaching your contacts’ inbox and not the spam folder.
These protocols have become the standard in the email world. A message sent without DKIM and/or SPF may be considered suspicious by the different email analysis tools.
How does DKIM work?
This part can get a little tricky, so if you just want to get this over with and learn how to set up DKIM, you can skip to the next section and find the instructions for your operating system and DNS provider.
DKIM is sort of like hunting for a hidden treasure. Except it’s not you doing the hunting. It’s the server receiving your emails. The server is looking for a ‘public key’ that will allow it to confirm the email sender’s legitimacy.
Setting up DKIM begins with the email sender – that’s you – selecting the email fields you want included in your DKIM signature. This could be the subject, body, from, pre-header, etc. You do this because if any of these get altered while the email is in transit, even by just a single character, DKIM authentication will fail. You set this up one time. You don’t have to do it every time you send an email.
Then, when you do send an email, your email server will generate what’s known as a ‘hash value,’ which is like a coded version of the fields you’ve selected. This hash value appears in the email header, and this is what is referred to as the email’s DKIM signature.
The hash value itself gets encrypted with a private key, and only the email sender can access that key.
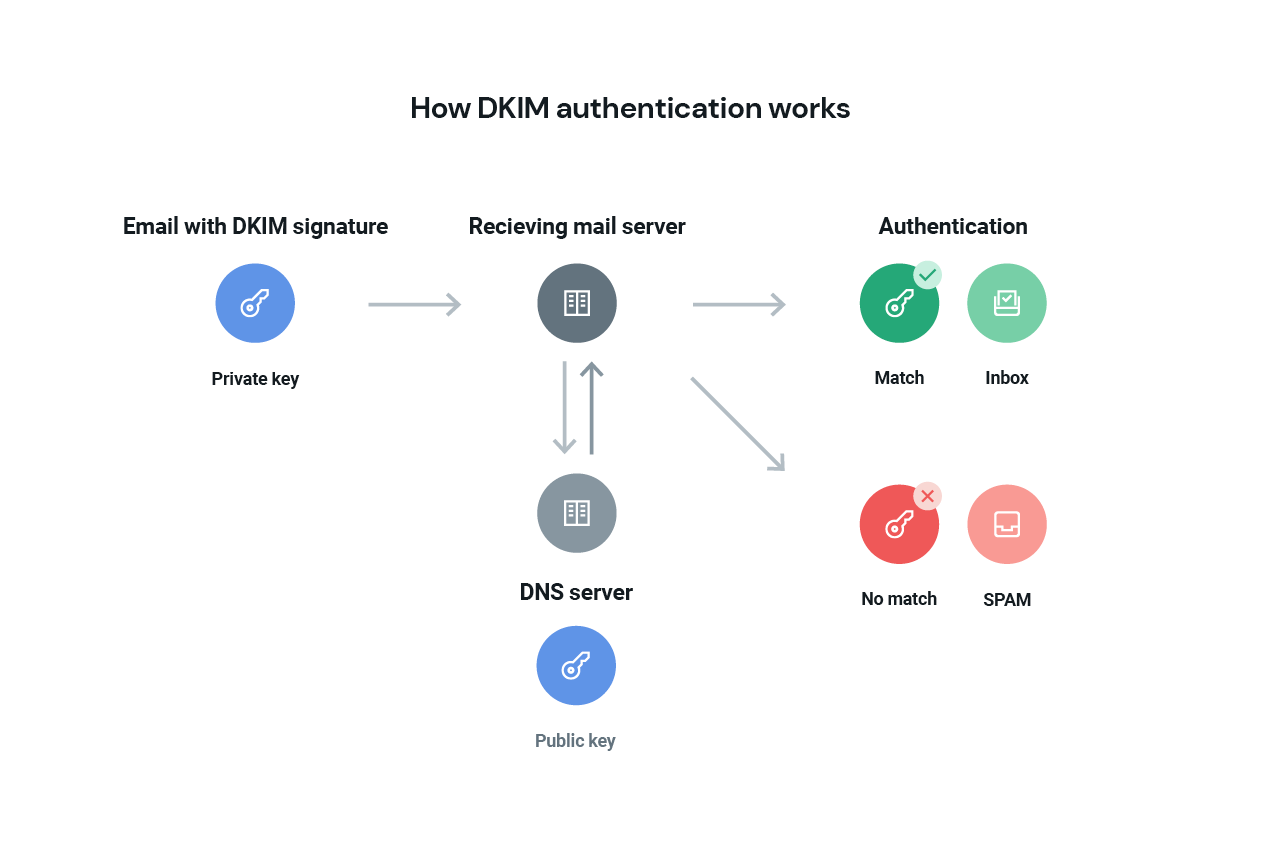
However, there’s another key – the public key – that the receiving email server can go find and use to unlock the DKIM signature. That’s the treasure hunt. Where is this public key? It’s in your DNS, and the receiving email server will look for your public key there. When you set up DKIM using the instructions below, you’ll end up in your DNS records, and this is why.
Once the receiving email server finds your public key, it must match the private key within your email header. If it does, this validates the email signature and confirms the legitimacy of the email and the sender. At that point, the hash value is decrypted, the server can verify the email hasn’t been altered, and it gets delivered. Check out this example of a DKIM signature.
DKIM encryption keys
DKIM keys come in various lengths, with 1024-bit and 2048-bit keys being the most common. The length of the key impacts how difficult it is for an attacker to crack the encryption. As it is with standard passwords, the longer the key, the harder it will be to break.
While 1024-bit keys is the standard cryptographic length used in DKIM email authentication, we highly recommend shifting to a 2048-bit key. At double the key length, 2048-bit keys provide significantly stronger encryption and are considered more future-proof.
All Sinch Mailjet users’ sending domains will now default to a 2048-bit DKIM authentication, while existing authenticated domains (1024-bit) can be updated to the new standard, providing enhanced security and reliability against sophisticated email threats.
What is a DKIM selector?
We’re getting into the weeds a bit here – the DKIM selector is how the receiving email server finds the DKIM public key. The selector tells the server where to find the key, and the selector is included as part of your DKIM signature in the email header.
Want to see your DKIM selector and verify you have set up DKIM correctly?
First, you can find the selector for your domain by sending an email to yourself. Open the email and view the ‘original message’, which might be referred to as the “raw message,” or the full header in some email clients. You’ll see the email header and can look for the DKIM signature and the s= value. That’s the DKIM selector.
Then, use your selector value in this DKIM inspector tool to confirm that you’ve set up DKIM correctly.
DKIM setup: How to configure DKIM in three simple steps
Follow the steps below to enable DKIM signing in your email messages:
Step #1: Setting up configuration of DKIM to generate the key pair
The tool of choice depends on your operating system. For Microsoft Windows you can use PUTTYGen – here’s a tutorial. For Linux and Mac, you can use ssh-keygen – Github has an excellent tutorial for this one.
Step #2: Placing the public key as a TXT record in the DNS settings
We have provided a list of DNS providers together with links to official and third-party documentation. They can help you with TXT and DNS record setup:
Amazon Route 53: SPF and DKIM
Bluehost: General DNS Setup
CloudFlare: Email Security DNS Wizard
Dreamhost: DKIM setup
DynDNS: General DNS setup
GoDaddy: SPF and DKIM
HostGator: General DNS setup
Hover: General DNS setup
Namecheap: DKIM setup
Network Solutions: General DNS setup
Register.com: General DNS setup
ZoneEdit: General DNS setup
Step #3: Generating and saving the signature
When using open source SMTP servers like Sendmail or Postfix, or any other SMTP server that supports milter, you can use a special milter ( = email filter), the DKIM milter. This milter has been released by Sendmail as open source and allows you to sign email headers with a generated private DKIM key. For more information, take a look at their extensive documentation.
How to set up DKIM with Mailjet
To define Mailjet as a legitimate sender for email campaigns, you must configure your SPF records and DKIM records for each of your sending domains.This can only be done on custom domains or domains that you own – you won’t be able to configure DKIM authentication on webmail accounts like Gmail, Hotmail, or Yahoo.
Setting up DKIM with Mailjet is very simple. Mailjet gives you the public key to register through your website host interface. There, you can integrate the public key into your registration area.
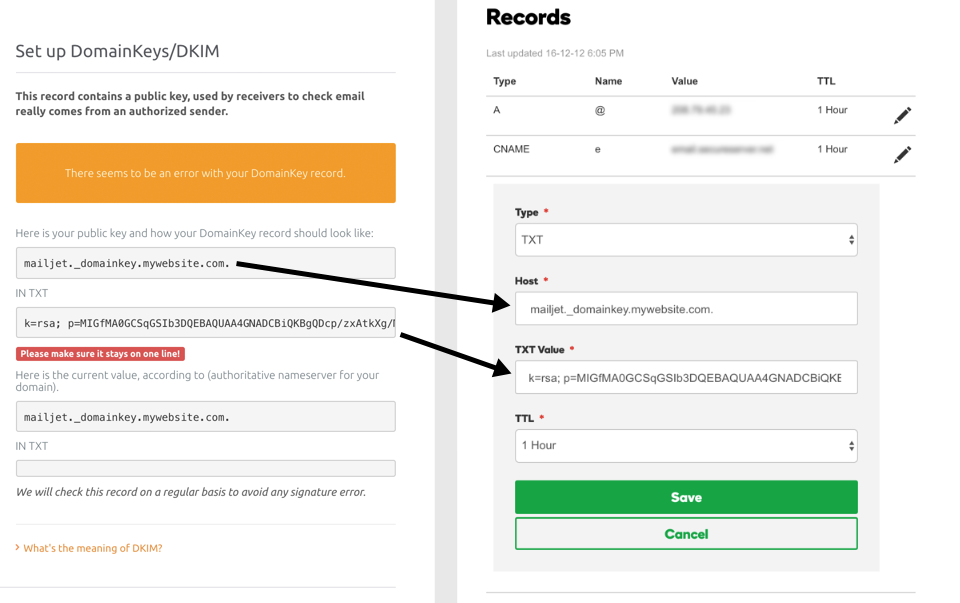
Don’t worry – if you need help, you can find all the necessary information and step-by-step processes in our documentation. It’s so complete, it even includes support guides for each of the main hosting providers (OVH, Gandi, Cloudflare, HostGator etc.).
Wrapping up
So there you have it. Hopefully, DKIM doesn’t seem too hard to follow anymore.
We now know DKIM is used to validate email senders and to protect your emails in transit. This allows the receiving server to use encryption tools that confirm the authenticity of the sender. You have all the tools and instructions to set up DKIM and confirm that you’ve done it correctly. But you can always go to the organization that laid down the framework –dkim.org – for more information.
Now that you know what DKIM is and how to implement it, you can move on to your SPF authentication and make real progress in improving your email deliverability.